This does not necessarily require data to be transferred to a host provider cloud. There are numerous options to provide remote access to your company’s resources for your remote workers, suppliers and customers. Just to mention a few examples that tend to come up on regards to remote work. Atlassian customers can choose between the Atlassian cloud and the on-premise setup in a data center of their choice. Most users have heard about Jira and Confluence. Most companies use those tools on-premise without access to the internet, because employees only need to access the services when they’re at work. Most users access internal networks via a VPN connection. The user utilizies a “secure tunnel” between the home office and the company network. It is crucial to strongly secure the user authentication at the VPN. This can be achieved by using the SecSign ID VPN Plugin for two-factor authentication. Another option to provide access to company resources for employees is a RDP. To secure access to the RDP a strong authentication is crucial, for example with the SecSign ID RDP two-factor authentication plugin. Every company has a couple recurring processes, mostly involving clearances. This includes for example approval of invoices, approval of resource access, multi-step approval processes, contract signing, counter-signing and more. The SecCommerce Server offers all this. You can decide if you want to keep the processes on-premise, or if a cloud setup is sufficient for your security requirements. Some of the most common scenarios include: With the SecPKI from SecCommerce and sign-me from the German Federal Printing Office you can ensure that no sensitive data needs to leave your infrastructure at any point. The users are automatically guided through the respective procedures, from registration to identification of the user and finally the signature. You can customize all steps in the process, including the design of the signature and positioning in the document. The documents that need to be signed can also be forwarded via a SAP- or HR-system, or via Email to start the signature process and workflow. This ensures the legal integrity of the process. There are numerous options to realize a signature workflow. The certificates and signatures for the first two individual A and B are created and managed via the SecPKI server. The user doesn’t need to worry about technical details like certificates at any point. Individual C can, after individuals A and B completed their advanced signature, sign the document with a qualified signature. To start this workflow, individual A receives an Email with a link and the invitation to sign the document. Once individual A successfully signed the document, individual B receives a link and invitation to sign the document via Email. You can decide individually if the users can access the document with a password, or if they need to authenticate with a two-factor authentication. Once individual B successfully signed the document, the document is forwarded to individual C. C is forwarded to the signature portal, “signs” the document which automatically creates the hash value. The hash value for the document is forwarded to for example sign-me. Individual C authenticates with sign-me and releases the signature via two-factor authentication. He is then forwarded to the signature portal, which automatically verifies the signature. This concludes the process. The successfully signed document can either be downloaded manually or it can be forwarded to the archive via an API. The server automatically creates an audit-proof inspection report. It verifies and logs the signature and access in every step. Simultaneously, it automatically creates a hash tree (LTA) to ensure an audit-proof long-term archiving. More information about multiple signatures used for workflows Sending and receiving invoices via Email is becoming more common. With the SecPKI server and a modul SMTP Mail Proxy you can automatically start predefined processes for every Email that is received. This may for example include the forwarding of respective invoices to a group of persons X, who need to verify and sign or release the documents. Digital solutions allow you to remain able to act in difficult times, without jeopardizing your company security and data at any point.
Current developments amid the Covid-19 pandemic pose a challenge to companies that normally rely on in-office employees. Rarely any company is set up to realize an exclusively digital workflow, much less to realize a secure remote workflow. The following article gives and overview of challenges that need to be conquered and solutions for a secure remote work setup.
The following questions need to be answered:
1. Can I securely remotely (for example from a Home Office) access all necessary information that I need for my work?
It is however crucial that remote access is secured with a sufficient encryption and a secure user authentication.
Atlassian (Jira, Confluence, Bitbucket)
With the SecSign ID plugins we offer a secure protection of those services within MINUTES. More information about the SecSign ID Atlassian plugins are available here. VPN
RDP
2. Are all processes, for example release of invoices or general approval workflows, possible from remote, or are they tied to paper-based procedures?
These processes require two factors: A system that regulates which person has to approve what at which time and – depending on the legal and security requirements – a simple, advanced and/or qualified signature or a qualified seal. Qualified remote signatures with SecPKI and sign-me
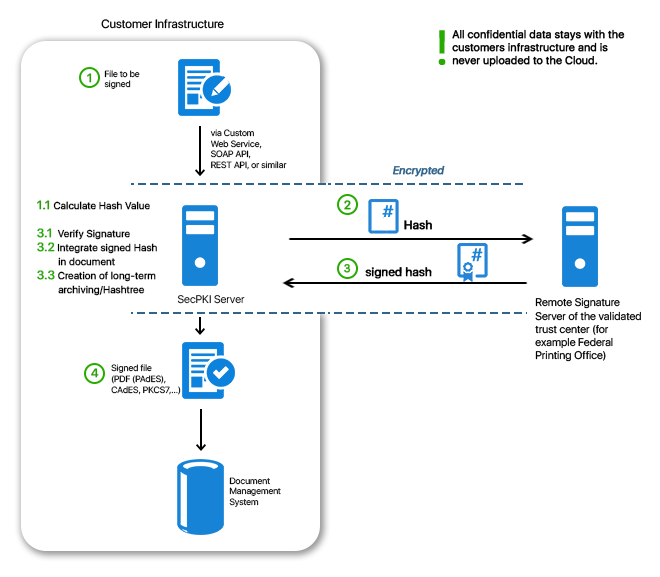
The SecPKI server allows you to create PDF, Word, XML and all other relevant data types. It also offers a signature portal that can be customized based on your requirements and procedures.
The SecPKI calculates the hash value of each document that is uploaded to the signature portal, and only this hash value is forwarded to the remote signature service. That way no sensitive data leaves your premises and even large files can be signed quickly. Signature-Workflows
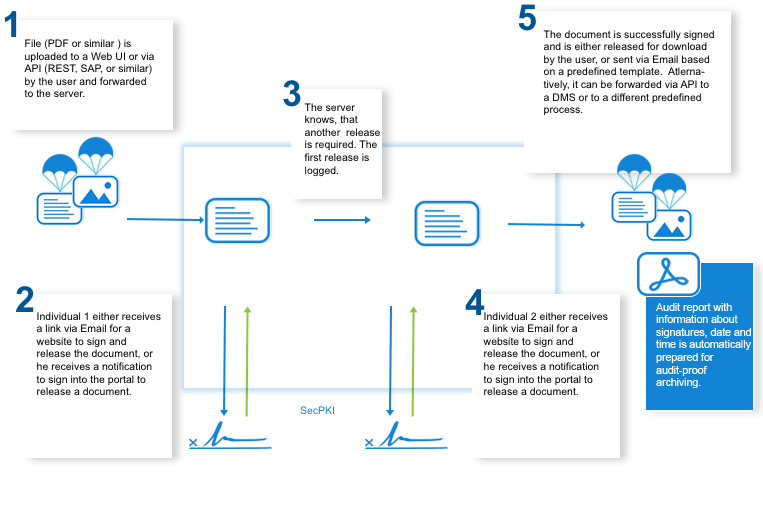
Assuming a document needs to be signed by three individuals (ABC), before it can be stored in the archive or forwarded to the SAP or booking system. The first two signatures don’t need to be qualified, they don’t need to satisfy the requirement of the written form – but signature C needs to. Still, the company wants to verify and ensure digitally that the data in the document remain unchanged and who completed the signing process. Thus, an advanced signature is required.
More information about long term archiving with hash treesDigital invoices in the inbox
SecCommerce
Menü
Electronic Signatures
- The Signature Portal
- Signature types
- Signature tools for end users
- FAQ (SecSigner)
- Signatures in web applications
- Substitute scanning and signing (e-records)
- Digital mailroom and digital signature for incoming mail
- Multiple signatures used for workflow
- Verification and creation of mass signatures or individual signatures on server side
- Long term archiving with hash trees
- Remote Qualified Electronic Signature
- Electronic Seal eIDAS
- Identity and Access Management IdM 2FA
Encryption
Private Cloud
High security and easy to use
Client Software
SecSigner
Create electronic signatures
SecCardAdmin
Administration of signature cards
Signatur Workflows
Signature Portal
Complex signature workflows with all signature types
SecArchive
Substitute scanning
SecPKI Server
Central server of several products
SecVerification Server
Verification & decryption
SecSigner Server
encryption & signature creation
Two Factor Authentication
SecRouter
Secures website access
SecAuthenticator
User identification
SecSignID
Two Factor Authentication
SecSignID Server
SecSignID on-premise solution
File storage & sharing
SecSign Portal Server
Secure messaging and file sharing