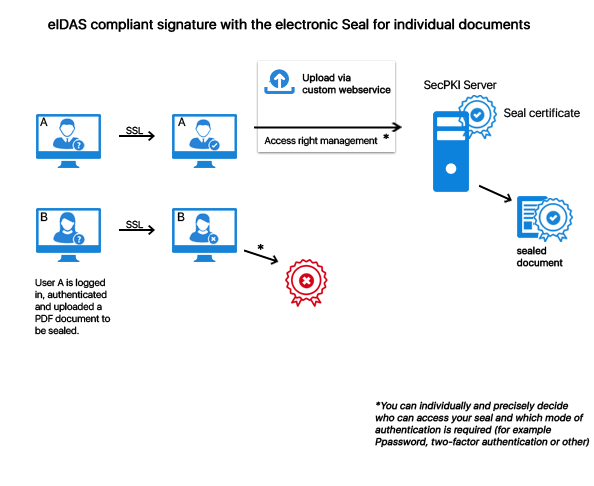
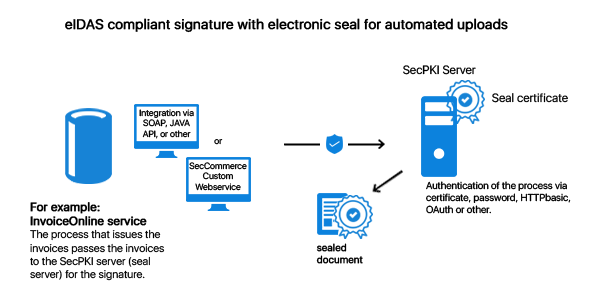
This means that for a qualified seal the certificate is issued in the name of a legal entity and not (as in case of a qualified signature) in the name of an individual person. A qualified Seal can be used as smart card (seal card), HSM or remote seal with our software. A qualified seal can guarantee at least two important aspects: The authenticity of the data (i.e. that they originate from the legal entity as claimed) and the integrity (that the data was not manipulated after the sealing process – e.g. statements of account or a notice from a public authority). What makes the qualified seal so special is that it can be used very conveniently for the signature on server side in order to seal files on server side (e.g. automated sealing of emails or statements of account). Qualified electronic sealing can be realized by using: On the sealing card the private key and the certificate of the authority/the company are located. A qualified seal can be generated via the client or on the server: File transfer by using: Precise control of access rights for: For the qualified electronic seal you can use our SecPKI Server (SecSign ID Server). You can operate the SecPKI Server either in your own data center or in a data center of your choice. By this all files remain on your server until they are signed and processed. The SecPKI Server manages the electronic seal centrally and provides you with an authorization management for the electronic sealing processes so that you can define on a finely granular basis which user or process is allowed to seal electronically. Documents from external programs are transferred in an automated way to SecPKI by using an authenticated process. You can, for example, define in the SecPKI Server that the process is authorized to seal all generated files electronically. Email attachments, invoices, prescriptions, etc. are, for example, transferred automatically. The electronic seal is created by individuals who have the required authorization in the SecPKI Server. According to the respective application you can decide on the authentication level for the approval of the electronic seal. All this is controlled and configured in the internal authorization management of the SecPKI Server (please also see “User management for the SecPKI Server”) As a result you can get a PDF signature with a stylish visual seal stamp and integrated signature as usual or a file with an external signature file. The signed PDF meets the European standards for qualified signatures (eIDAS). An internal signature is called PAdES signature. In case of an external signature it is called CAdES signature. Thus, you can simply transfer the PDF files from your process to the SecPKI Server directly via API calls (SOAP, REST, etc.) or via a monitored directory and seal them in an automated process. The position can be defined by using properties or form fields (PDF signature fields). The SecPKI Server verifies the signature and can, if desired, ensure the evidential value for the electronically sealed documents by using a hash tree (long-term archiving). The electronically sealed files can then be transmitted directly from the SecPKI Server to further processing and can, for example, be provided as download option to the users via the customer portal. Additionally, the SecPKI Server can provide you with a web service which can be used for the convenient manual electronic sealing of files by using the upload function. Furthermore, you can use the web service of the SecPKI Server for the verification of signatures and have your customers (by using your web service) verify the document to make sure that you are really the sender of the document. It is, of course, also possible to integrate the verification of signatures into your customer portal by using a REST Api. The operator of the server can exactly define if, when, and how a process/user/user group is allowed to seal electronically. It can also be clearly defined if access is only allowed, for example, after a two-factor authentication or only with a specific computer. Important note: The factors for the authentication are not the same factors as for the seal card (the sealing process can be directly activated at the workstation of the authorized employee). The authentication here is required for each single document, respectively, document batch, which should receive a qualified seal. The SecPKI Server can also make the generation of electronic seals available for external users/employees. The access can be protected via two-factor authentication. For an easier enrollment SecPKI Server and user management can be connected directly with the existing identity management by using standardized interfaces. The administration of the seal cards and remote signature provider takes place via the admin interface of the SecPKI Server. If an employee should no longer be authorized to seal electronically, the authorization management provides you with the option to make the appropriate changes without the need to replace the relevant seal card. For example, the user logs into a web service and uploads a PDF file in order to have it electronically sealed. The access to the seal is additionally protected by detailed access rules which can be individually defined, e.g. by a 2FA. Only after a successful authentication against the SecPKI sealing server the document receives the seal certificate. Invoices are automatically transferred by the process creating the invoices to the SecPKI sealing server. The process transmission is carried out by, for example, SOAP, REST Api or Java Api. For this the process authenticates, for example, by using certificates, password, oAuth or other authentication processes. Only after a successful authentication of the invoicing process the documents receive the seal.
The benefit of the seal is that the server, which is used for the sealing of the documents, can (and should) manage the authorized users, respectively, the access to the seal via its authorization management. By this no user must enter a PIN for the signature card anymore (please see more about authorization management further down below). It is, of course, also possible to sign directly with the seal at the individual workspace by using client software (SecSigner).
Generation of Qualified Seals
Generating Electronic Seals With SecPKI Server

User Management With SecPKI Server
SecCommerce
Menü
Electronic Signatures
- The Signature Portal
- Signature types
- Signature tools for end users
- FAQ (SecSigner)
- Signatures in web applications
- Substitute scanning and signing (e-records)
- Digital mailroom and digital signature for incoming mail
- Multiple signatures used for workflow
- Verification and creation of mass signatures or individual signatures on server side
- Long term archiving with hash trees
- Remote Qualified Electronic Signature
- Electronic Seal eIDAS
- Identity and Access Management IdM 2FA
Encryption
Private Cloud
High security and easy to use
Client Software
SecSigner
Create electronic signatures
SecCardAdmin
Administration of signature cards
Signatur Workflows
Signature Portal
Complex signature workflows with all signature types
SecArchive
Substitute scanning
SecPKI Server
Central server of several products
SecVerification Server
Verification & decryption
SecSigner Server
encryption & signature creation
Two Factor Authentication
SecRouter
Secures website access
SecAuthenticator
User identification
SecSignID
Two Factor Authentication
SecSignID Server
SecSignID on-premise solution
File storage & sharing
SecSign Portal Server
Secure messaging and file sharing