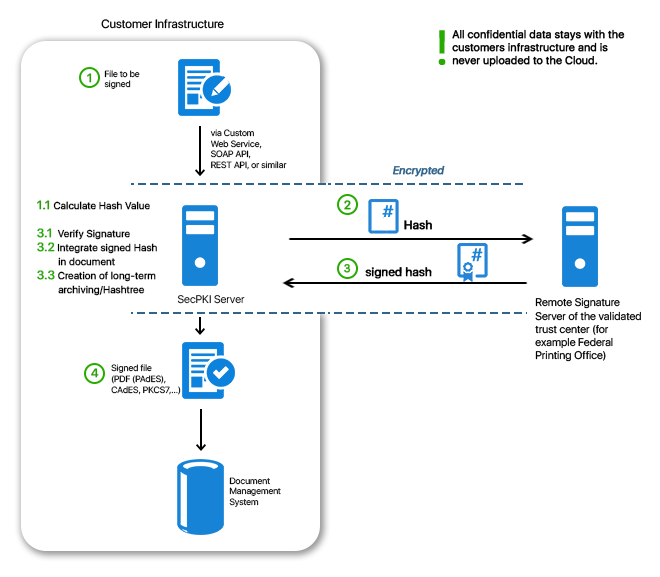
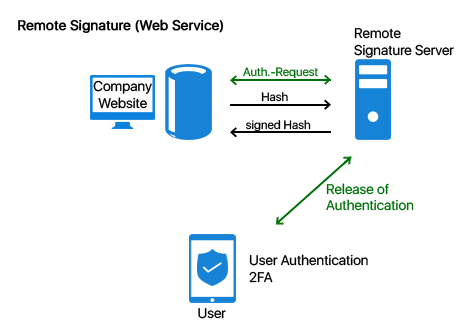
By using remote signatures the qualified signature can be easily integrated into the day-to-day business. Thanks to secure authentication and the SecPKI Server qualified signatures can be realized securely and conveniently. In Germany it was only possible to create a qualified signature with a signature card until the introduction of remote signature services. It was not always easy to integrate the use of a signature cards as well as the required card readers into any business process. Apart from the fact that the handling was extremely uncomfortable for the user it was also quite difficult to integrate the required software into the procedures. And what about an enterprise requiring the signature of a customer or an external partner? One can hardly force customers or partners to buy signature card and card reader for this purpose… The above mentioned issues, however, are no problem anymore with the remote signature and new identification procedures like VideoIdent. The SecPKI Server can be used for the remote signature with a qualified signature. With the SecPKI Server you can comfortably create qualified signatures in each application or via any website. At the same time you do not have to take care about the connection to the remote signature service of the validated trust center. All this will be done by our pre-configured SecPKI Server. You have various options how to use the remote signature. Option A: Via a custom web service offered to you by the SecPKI Server. In this case you do not have to make any implementations but will receive a web service which is designed according to your wishes and requirements in the look and feel of your company (e.g. with your URL) Option B: You integrate the API calls into your own service. For this purpose we can provide you with various API´s and interfaces (e.g. REST or SOAP) If you use a remote signature service, the SecPKI Server as well as our signature component SecSigner do not only take care of the linkage to the remote signature service but additionally makes it possible that you have to send only a hash value (i.e. a non-confidential string) to the remote signature service. Maybe the volume of your data is is too large to send it via internet? Another advantage of the SecPKI Server is that the hash value is not larger than only a few KB, even if the file has a size of several MB or even GB. Due to this fact the procedure is additionally extremely performant. If you require only advanced signatures, this can be also easily realized with the SecPKI Server. The SecPKI Server can, for example, easily read data records from an Active Directory and create advanced certificates with it, which will then be used for the signatures by the SecPKI Server. Furthermore, it is, of course, also possible to create the users directly in the server by using the SecPKI dashboard. We can provide you with numerous options. In case of any questions, or if you would like to receive more advice please do not hesitate to contact us . The SecPKI Server receives the signature from the remote signature server, verifies the signatures and uses the successfully verified signature in order to build the long-term archive. The evidential value of the signature is thus directly secured. More information You transfer the file you wish to have signed to the SecPKI Server (eg. PDF, XML, Word, etc.). The user uploads this file either manually (e.g. via drag-and-drop) into the custom website of the SecPKI Server, or you transmit the file to the SecPKI Server by using a simple API call. The SecPKI Server calculates the hash value of the file and sends the hash value to the remote signature service. The user authenticates for the remote signature service with password and user name and confirms the wish to sign by using a two-factor authentication (e.g. SMS code). It is the decision of the operator of the remote signature service which two-factor authentication can be used for this purpose. The signed hash value is returned to the SecPKI Server which verifies the signature, enters the signatures hash value into the hash tree and transmits the signed file, eg. to the DMS or a web service for further processing. The SecPKI Server can sign PDF´s with an integrated signature. This means it integrates the signed hash value into the PDF so that you will have a PAdES signature in the end. For this the SecPKI Server has – like the SecSigner – a full PDF parser. The SecPKI Server analyses the complete structure of the PDF and can thus integrate the visible signature batch automatically into the proposed form fields of the PDF. Thus, the SecPKI Server can also realize signature workflows in PDF´s when different individuals have to sign using different form fields. The signed PDF is thus compliant to the standard and meets all requirements of Adobe. Furthermore, the SecPKI Server can position a visible signature batch on the PDF. The used information can be configured as wished (e.g. company logo, information of the certificate, address, etc.). Options for the positioning of the signatures note: You probably wonder whether you can and wish to trust an external server with your highly critical business data, which includes sending the data via internet to the server and to accept connections to a cloud – even if the external server belongs to a validated trust center. The solution: Operate the process in your own data center by using the SecPKI Server which is operated by yourself in your own company. By this you get a server software with all required software components. The advantages are obvious: The files never leave the company server. The SecPKI Server is the central contact for your own customers so that they do not have to get used to a new, unknown service. The SecPKI Server is able to generate certificates itself. The key material can be secured in an HSM. It is also possible to communicate with other sign units via the SecPKI Server. Furthermore, the SecPKI Server provides you with a full authorization and identity management. This can be used in order to define different mechanisms for the access protection, covering simple password logins but also highly secure two-factor authentication (2FA). A qualified remote signature requires a 2FA which can be provided by the SecPKI Server. Additionally, the server is able to connect different identification services. Please note: If you wish to operate your own qualified remote signature service, you have to have yourself to be certified as operator. Short overview of the advantages: Via its dashboard the SecPKI Server provides the option to define any kind of signature sequences. For example, it can be defined that individual A has to sign before individual B. Only after A and B have signed, the document can be released for further processing. You have several options in the SecPKI Server how to create the concrete signature. Most popular is the signature with a software certificate created for the user (for advanced signatures) which is saved by the SecPKI Server for the user or – as mentioned above – a signature by using a remote signature service (for qualified signatures). The certificates of the SecPKI Server are appropriate for advanced signatures. For this scenario the users who are supposed to sign are created just once. It is also possible to connect the SecPKI Server directly with an Active Directory (AD). The easiest introductory case is that the users are generated in the SecPKI Server by an administrator. This can be easily and comfortably done by using the SecPKI dashboard. The SecPKI Server provides you with a website so that you get the user as well as the certificate for this user (like for a simple user profile generation). After the user was created, the most frequently used option is to generate a template for a specific signature sequence, e.g. two individuals have to sign a document before it is authorized for further processing. Then, users or user groups can be assigned to this template. After the generation all individuals possess an account on the SecPKI Server and can – depending on the specific authorization – use existing workflows or create new workflows or are, for example, only allowed to create a document in the workflow process. For the authentication you can choose from various options: After the signature of the first employee, the second employee receives an email with the link and can now sign the document as well. After the workflow is successfully completed the document can, for example, be sent by the SecPKI Server to another email address and can be written into a shared folder. For additional general information please also see the following link. Depending on the requirements a company uses either advanced or qualified signatures. If the signed documents must be verifiable (with regard to authenticity, inalterability of the data, and origin), the signature which is created via a remote signature service must be verified directly before storing in order to prevent that invalid files get to the archive. During this verification the hashtree for the renewal signatures can be built in order to keep the evidence value of the sigatures. The verification step should best be done automatically with a service in your infrastructure. This way you do not only make sure that the signature is correctly processed but also that no damage can take place during the transmission between the services. In this context you will often come across terms like hash tree, renewal of signature, time stamp, and long-term archiving. Even though this might sound like a tremendous and time-consuming effort you do not have to worry. With our SecPKI Server these are completely automated processes.Content

Remote Signature vs Qualified Signature With Signature Card
Overview of Advantages of SecPKI Server in the Context of Remote Signatures via an External Remote Signatures Service
Using SecPKI, SecSigner & Co. For Signature With a Remote Signature Server
Process Of a Remote Signature When Using an External Remote Signature Service By SecPKI Server
PDF Signature With Visible Signature Batch
Operating an On-Premise Remote Signature Service
You can integrate the remote signature easily and conveniently into any process by using our API´s. If desired, we will also be happy to provide you with a complete web service designed in your company´s look and feel.Signatures In Workflows (e.g. Authorization According To Four-Eyes Principle)

When a document is uploaded to the existing workflow (e.g. via an API or – in a first step – via a website provided by the SecPKI Server) individual A receives an email by the SecPKI Server with a link to the document which is to be signed. After individual A opened the link the document can be viewed in the browser, and employee A can sign it with a simple click. The user authentication for this step depends on the required and desired security level.Authentication Options

The Use Of Signatures For Electronic files and Digital Inbox (Long-Term Archiving)
SecCommerce
Menü
Electronic Signatures
- The Signature Portal
- Signature types
- Signature tools for end users
- FAQ (SecSigner)
- Signatures in web applications
- Substitute scanning and signing (e-records)
- Digital mailroom and digital signature for incoming mail
- Multiple signatures used for workflow
- Verification and creation of mass signatures or individual signatures on server side
- Long term archiving with hash trees
- Remote Qualified Electronic Signature
- Electronic Seal eIDAS
- Identity and Access Management IdM 2FA
Encryption
Private Cloud
High security and easy to use
Client Software
SecSigner
Create electronic signatures
SecCardAdmin
Administration of signature cards
Signatur Workflows
Signature Portal
Complex signature workflows with all signature types
SecArchive
Substitute scanning
SecPKI Server
Central server of several products
SecVerification Server
Verification & decryption
SecSigner Server
encryption & signature creation
Two Factor Authentication
SecRouter
Secures website access
SecAuthenticator
User identification
SecSignID
Two Factor Authentication
SecSignID Server
SecSignID on-premise solution
File storage & sharing
SecSign Portal Server
Secure messaging and file sharing