Afterwards, SecRouter requests the rights of the authenticated user from the SecPKI server. If the user has the required rights in the SecPKI server, and if the user´s certificate is not locked in the trust center, his browser receives a session cookie from SecRouter, and the user is redirected to the protected website. The login process has now been completed. As an alternative to redirecting to a website with session cookie, the website, which should be protected, can be arranged behind SecRouther in the internal network. In this case all HTTP requests run after the verification of the authorization through SecRouter. The protected website can request the user´s identity and – if necessary – the user´s rights from the SecPKI server by the SecPKI API. The SecPKI API can be invoked via SOAP or can be integrated directly in Java. Java and SOAP samples are included. If you have a signature card or a software certificate, we recommend a login on our SecRouter live demo. Please select there first the link for initial registration. We will activate your login immediately. With the eService of Deutsche Rentenversicherung Bund (German pension insurance institute) you can see SecRouter and SecAuthenticator in action. The solution has been used productively for many years now. If you have a statutory pension insurance, you can immediately view your pension account by using the eService. We will be happy to advise on the implementation of SecRouter and SecAuthenticator in your company.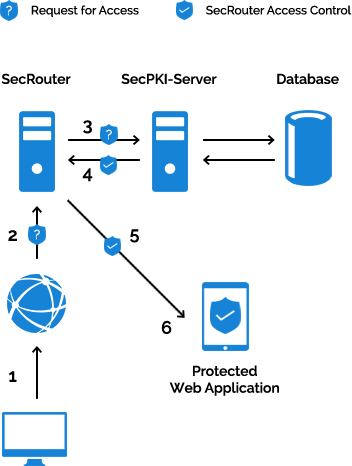
Secures website access and identifies the users for the website by signature card or software key. The image shows the construction of the system.
The user first installs the SecAuthenticator once on their computer. The SecAuthenticator registers itself as the responsible program for files with the secauthwr extension.
When you access a protected website, the browser is redirected to the SecRouter. This generates a secauthwr file with a session ID and passes it to the browser for download. The browser starts the installed SecAuthenticator. The SecAuthenticator receives the session ID from the secauthwr file and reads the user’s signature card or software key. The card reader and signature card used are automatically recognized. The SecAuthenticator then establishes a TLS-secured connection to the SecRouter. The user authenticates himself by entering his PIN on the card reader. Meanwhile, the protected website asks the SecPKI server whether the session has already been authenticated by the user. Once this occurs, the website receives the logged in user’s authentication certificate.
SecCommerce
Menü
Electronic Signatures
- The Signature Portal
- Signature types
- Signature tools for end users
- FAQ (SecSigner)
- Signatures in web applications
- Substitute scanning and signing (e-records)
- Digital mailroom and digital signature for incoming mail
- Multiple signatures used for workflow
- Verification and creation of mass signatures or individual signatures on server side
- Long term archiving with hash trees
- Remote Qualified Electronic Signature
- Electronic Seal eIDAS
- Identity and Access Management IdM 2FA
Encryption
Private Cloud
High security and easy to use
Client Software
SecSigner
Create electronic signatures
SecCardAdmin
Administration of signature cards
Signatur Workflows
Signature Portal
Complex signature workflows with all signature types
SecArchive
Substitute scanning
SecPKI Server
Central server of several products
SecVerification Server
Verification & decryption
SecSigner Server
encryption & signature creation
Two Factor Authentication
SecRouter
Secures website access
SecAuthenticator
User identification
SecSignID
Two Factor Authentication
SecSignID Server
SecSignID on-premise solution
File storage & sharing
SecSign Portal Server
Secure messaging and file sharing