Central SecPKI server
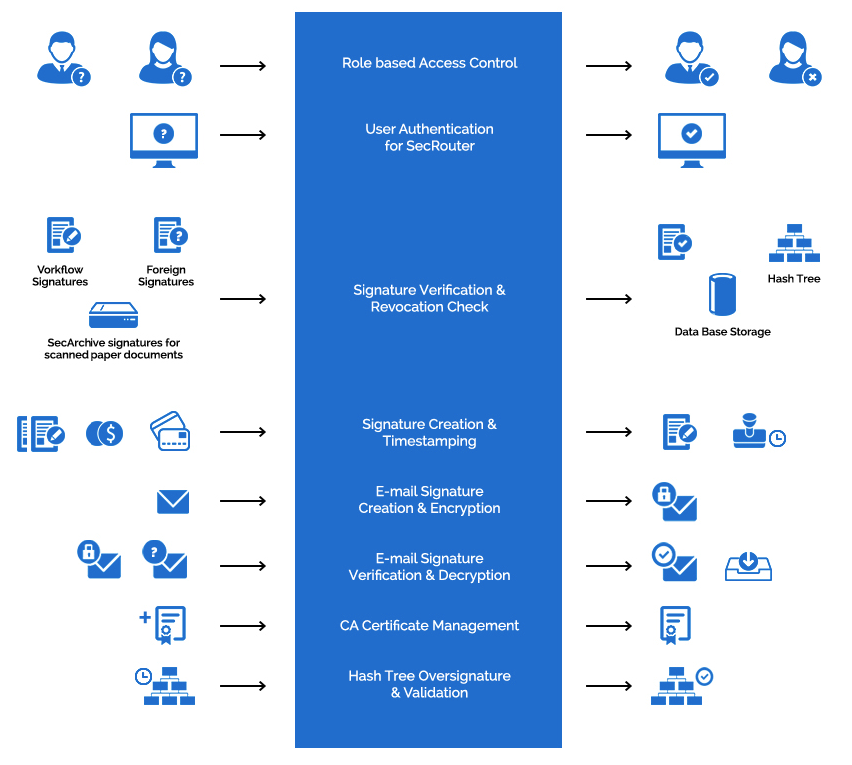
SecPKI server is the central element of several products by SecCommerce. It provides an administration which is multi-client capable for users, trust center services and access rights. The essential features of the SecPKI server are:
- Verification and audit-proof long-term archiving of signature data like hash values, OCSP certificate verification and time stamps. The SecPKI server especially verifies electronic signatures:
- for scanned paper documents coming from SecArchiveClient ,
- for procedures of workflow applications with an integrated SecSigner ,
- for received and sent emails,
- for files which were signed by other manufacturers.
- Audit-proof long-term archiving of documents according to ArchiSig. This electronic long-term archive secures archived documents and signatures from the loss of evidential proof of the used algorithms by the entry into hash trees and by obtaining trust center time stamps for the hash trees. The SecPKI server uses exclusively adequate international standards in combination with the appropriate cryptographic algorithms according to the federal network agency All archived data are re-signed before the expiration of the qualification of the algorithms and therefore always maintain their evidential proof. In this long-term archive the results of the online verification of the signatures by the trust centers and – if necessary – the assigned legal time stamps are archived as well all transaction data and their electronic signatures.
- Mass signature on server side. Signatures are generated by any number of signature cards and/or software certificates. The SecPKI server signs:
- Emails: The SecPKI server receives emails via an SMTP port directly from standard email clients like Thunderbird or Microsoft Outlook or from ERP software (e.g. for the signing of invoices). The selection of the emails, which are meant to be signed, takes place via configurable rules.
- Files in directories: The SecPKI server controls configurable directories and signs files which were stored there. Different signature cards can be used, and signatures with different options or formats can be created for each directory.
- Documents which are transmitted via the SecPKI API: Via the Java-API SecPKI API the signature invocation can be integrated into programs. The caller defines the signature options, the desired format as well as the signature cards and/or the software keys which are supposed to be used.
- Signatures can be created in the following formats:
- CMS (PKCS#7) SignedData
- XML-DSig
- integrated in PDF documents
- Request of time stamps: After the signing of the documents the SecPKI server gets optionally a time stamp from a configured trust center for every signature.
- Encryption: The SecPKI server encrypts individually after the signature generation:
- Emails: The SecPKI server receives emails via an SMTP port directly from standard email clients like Thunderbird or Microsoft Outlook or from ERP software (e.g. for the signing of invoices). The selection of the emails which are meant to be signed takes place via configurable rules, e.g. depending on the email address of the recipient.
- Files in directories: The SecPKI server controls configurable directories and signs files which were stored there. For each directory different recipient certificates can be defined.
- Documents which are transmitted via the SecPKI API: Via the Java-API SecPKI API the signature invocation can be integrated into programs. The caller defines the signature options, the desired format as well as the signature cards and/or the software keys which are supposed to be used.
- Decryption: During signature verification the SecPKI server recognizes encrypted files and decrypts them automatically, if the required signature card, respectively software certificate is available.
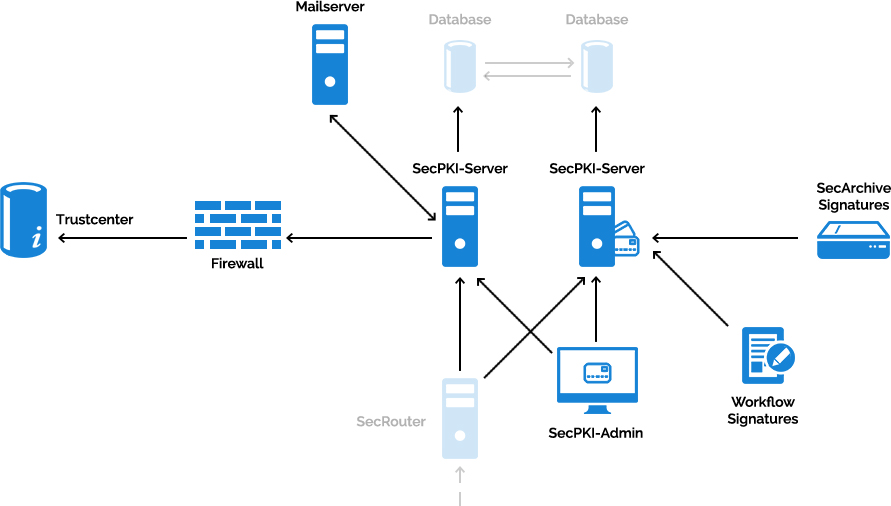
- User administration based on certificates and roles. With X.509-certificates you can create users in the SecPKI server. The Java applet SecPKISignOn enables the users to read their certificate directly from their signature cards, respectively software certificates and to transmit it to the SecPKI server. An administrator assign them to user groups. Depending on which group the user belongs, the user has certain rights to execute functions in the SecPKI server. The administrator defines the user groups authorized for certain functions. For standard cases like SecArchive scripts are included for the implementation of the groups.
- Verification of the authorization for SecRouter. The SecPKI server decides on basis of the group membership, if a user in in the internet is allowed to log into SecRouter and which websites the user is allowed to access.
- Trust center administration. CA-certificates as well as blacklist URL´s of relevant German and partly European trust centers are kept up to date by SecCommerce and are distributed via signed certificate batches to the SecPKI installations. The administrator for the respective client in the SecPKI server selects which of the offered trust centers should be allowed. Customer specific trust centers can be supplemented. The central list of trust centers can be extended on request.
- Time-controlled automatic execution of processes. In configurable intervals the SecPKI server carries out, for example, the following processes:
- Retrieval of blacklists from trust centers
- Examination of all user certificates as to blocking
- Retrieval of time stamps for new ArchiSig hash trees
- Consistency check of all ArchiSig hash trees and renewal signatures
- Retrieval of a CA certificate batch from SecCommerce
- Signing of emails
- Signing of files in directories
- Signature verification of files in directories
SecPKI server functionality
SecPKI API
SecPKI API is designed to integrate the SecPKI server services into other server or client applications.
From verification of mass signatures and integration of trust center services to the administration of user authorization you can extend your applications fast and with little integration effort. Examples for invocation of the SecPKI API methods in Java and sample SOAP requests are included. In order to enable the use of its function via SOAP, the SecPKI generates a WSDL description. Thus, SecPKI functions can be invoked:
- in Java and/or
- via SOAP requests
The invocations are transmitted using TLS encryption.The SecPKI server as well as the Java SecPK API on client side support:
- SSL 3.0
- TLS 1.0
- TLS 1.1
- TLS 1.2
Only the following, secure modes (Ciphersuites) are supported for an encrypted and integrity protected transmission:
- TLS_RSA_WITH_AES_256_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA
- RSA_3DES_EDE_CBC_SHA
The SecPKI server only executes SecPKI API invocations, if the caller is authorized. The caller therefore authenticates with an X.509-certificate via TLS-client authentication or with name and password.
SecPKI architecture
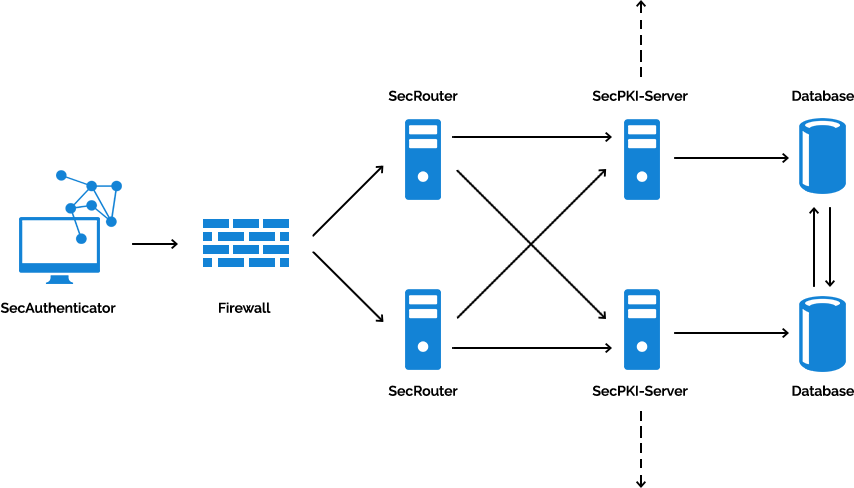
The SecPKI system is implemented in a multi-tier architecture. Central part of the multi-tier architecture is the SecPKI server which is connected via JDBC with a database instance.
The SecPKI server is administered via a Java applet which is available on a web server in the intranet. The SecPKI admin applet is designed for the initial installation of master data and accesses. It communicates directly with the SecPKI server (load-balancing capable) in a separate, TLS protected connection. The image additionally shows as sample application for SecPKI the component SecRouter (option) for access protection on websites.
Signature Portal
SecPKI streamlines your document workflows and provides secure electronic signatures. With the Signature Portal, you can utilize all eIDAS signature levels—whether signing critical business documents or creating complex workflows.
Learn more about the Signature Portal



